Threat-Led Penetration Testing - The New Norm
In Cybersecruity, Penetration Testing is the process of assessing computer systems against security weaknesses such as vulnerabilities and misconfigurations. It has been around for many years and is a widely-adopted practice within large and medium-sized organizations. Penetration Testing activities, or Pentests, are usually limited in scope, focusing on a subset of systems at a time. They also can be conducted from different perspectives; i.e., external, internal, and/or authenticated. These perspectives are referred to by black box, grey box, and white box.
Threat-led Penetration Testing is a new approach that is mandated by the European Digital Operational Resilience Act or DORA which applies to the financial sector. Unlike traditional Penetration Testing TLPT uses Threat Intelligence that is relevant to the company. In other words, testing is planned for based on collected Tactics, Techniques, and Procedures (TTPs) that threat actors use to target their victims. And since TTPs change, so does the test scope. In this way, TLPT becomes a cyclical process and is required at least every three years. Another important aspect of TLPT is that it focuses on pillar applications or critical systems as defined by the business. In this way, it provides tailored and risk-informed data about the security and compliance of computer systems. Figure 1 outlines differences between PT and TLPT.
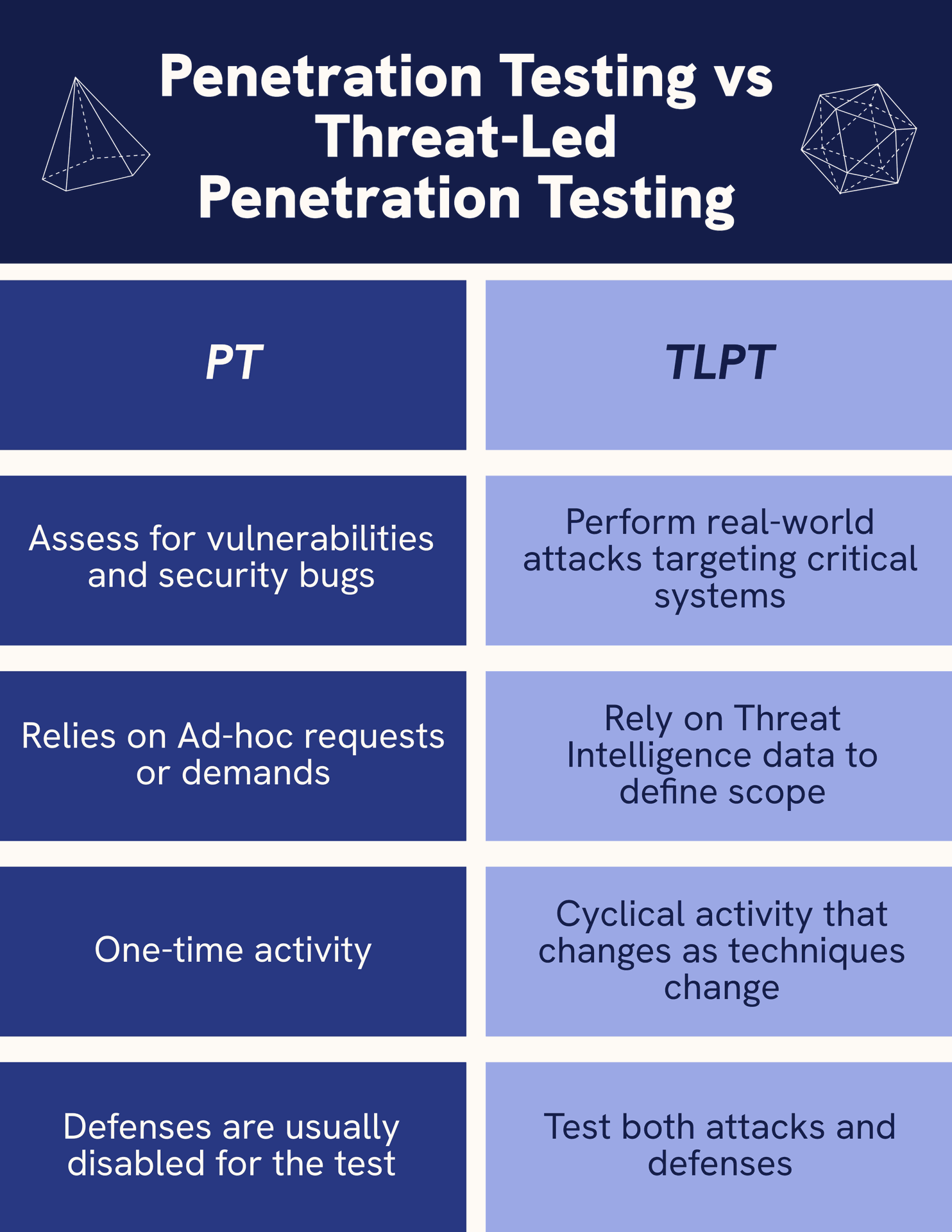
Illustration 1: Differences between Penetration Testing and Threat-Led Penetration Testing
The recent supply chain attacks caused by major Information and Communication Technoloy (ICT) providers calls for expanded Penetration Testing activities. In TLPT, ICT providers for financial actors in the European Union are also required to be subject to the testing. This means that the entire supply chain is tested for emerging attacks.
To guide the adoption of TLPT, the EU mandates financial institutions to adopt the TIBER-EU Framework. TIBER stands for Threat Intelligence-Based Ethical Red-teaming and provides a timeline for conducting TLPT consisting of three phases: Preparation, Testing, and Closure, with testing broken down into two sub-phases – Threat Intelligence then Red Team. Figure 2 illustrates TIBER-EU's workflow.
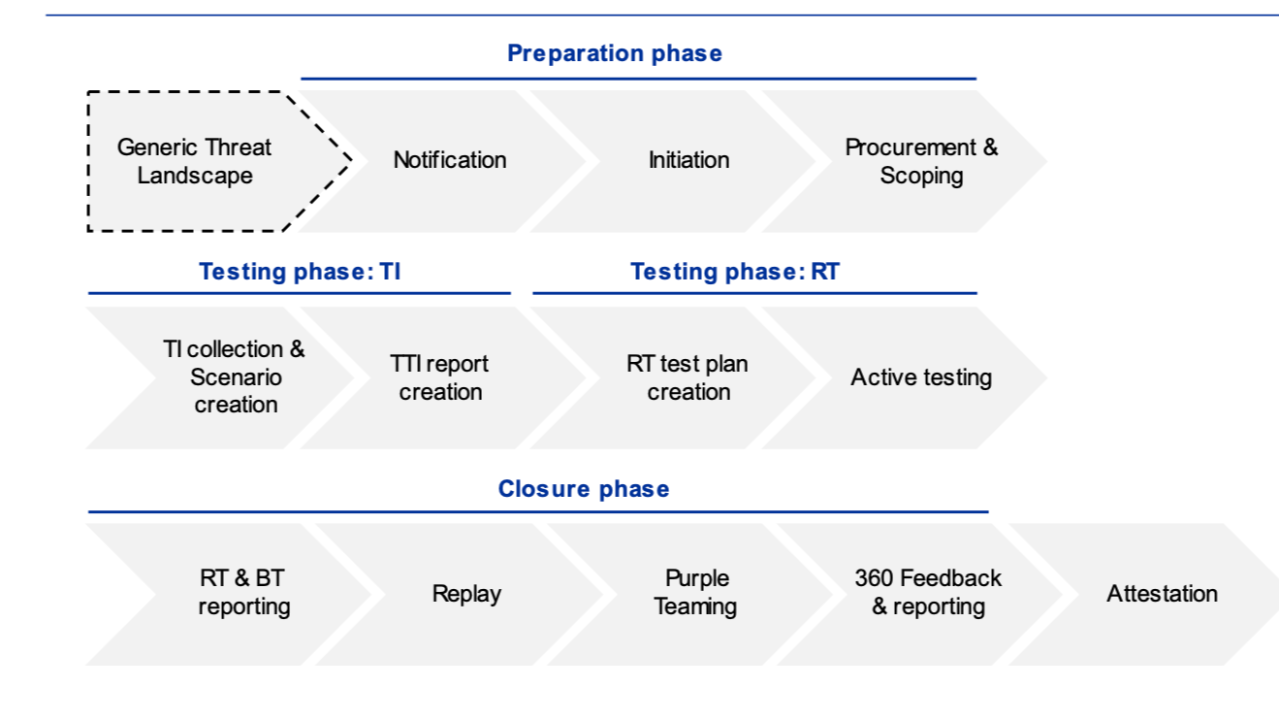
Illustration 2: TIBER-EU Framework Phases for Threat-Led Penetration Testing
TLPT is an exciting new chapter in cybersecruity and can proactively protect against emerging threats such as Advanced Persistent Threats (APTs). Businesses are encouraged to use it to structure their assessments and audits and enhance their effectiveness.